PKI and the Quantum Threat Timeline
Classical PKI Algorithms Must have Cryptographic Agility
Important considerations for Quantum Awareness in 2024 and beyond
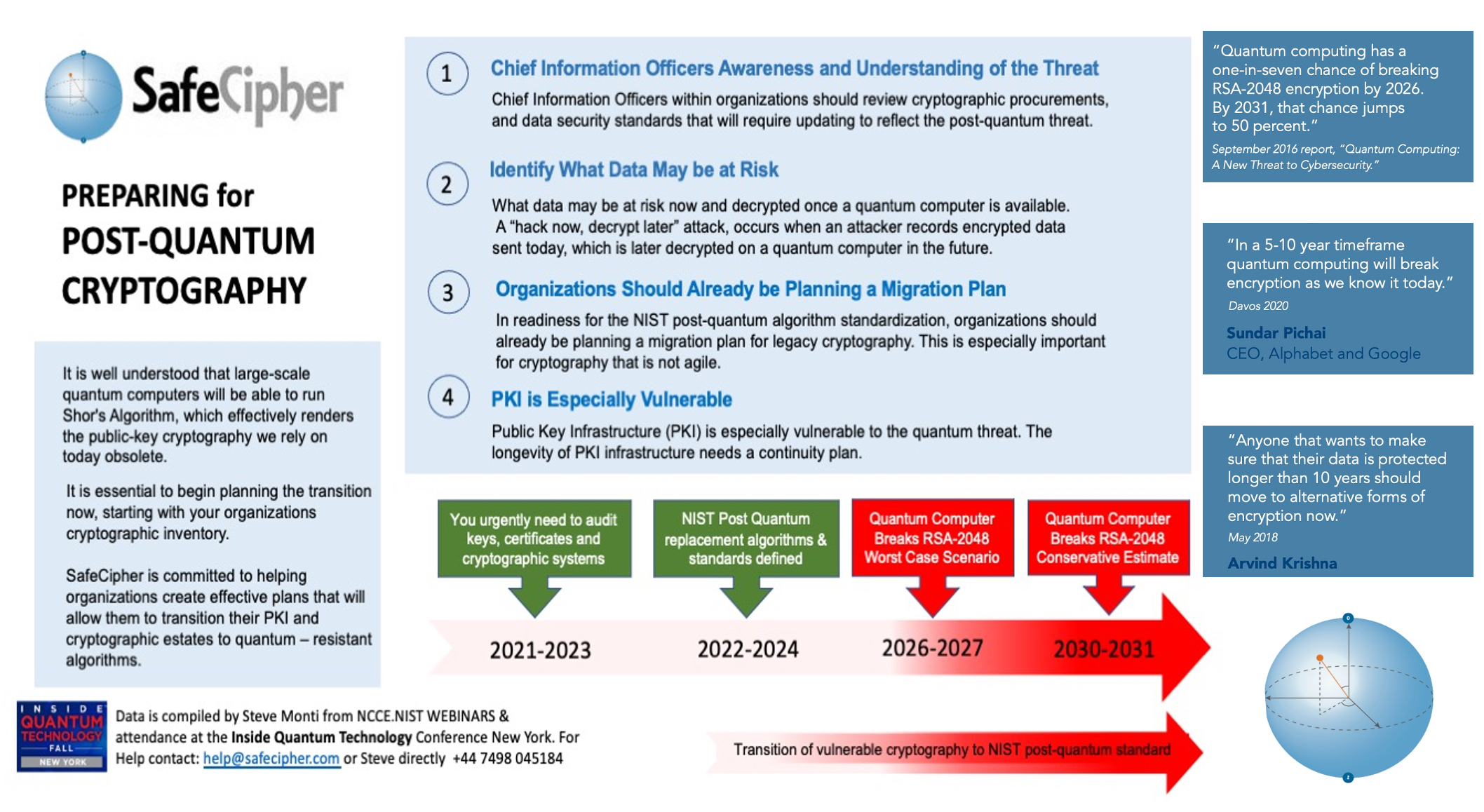
The above image, outlines four key points, regarding the preparation for post-quantum cryptography, as well as a timeline for transitioning to quantum-resistant algorithms. The points are further summarized below :
Chief Information Officers Awareness and Understanding of the Threat
Chief Information Officers (CIOs) within organizations are encouraged to review cryptographic procurements and data security standards that may need updating to address the emerging post-quantum threat. This point emphasizes the importance of awareness at the senior management level about the potential risks posed by quantum computing to current encryption standards.
Identify What Data May be at Risk
It’s crucial to determine which data could be compromised once a quantum computer becomes available. The graphic mentions the possibility of a “hack now, decrypt later” attack, where adversaries collect encrypted data today with the intention of decrypting it once quantum computing becomes sufficiently advanced. This underscores the need for proactive risk assessment of sensitive data.
Organizations Should Already be Planning a Migration Plan
Organizations are advised to start planning for the transition to post-quantum cryptography in response to the NIST (National Institute of Standards and Technology) post-quantum algorithm standardization. The process should include creating migration plans for legacy cryptography, which is especially vital for cryptography that is not agile or easily updated.
PKI is Especially Vulnerable
Public Key Infrastructure (PKI) is noted to be particularly at risk from quantum computing. The longevity of PKI infrastructure requires a continuity plan to transition to quantum-resistant algorithms.
X
Timeline for Transition
The timeline arrows above, indicate an urgent need to audit keys, certificates, and cryptographic systems between 2021-2023. By 2022-2024 (now), NIST post-quantum replacement algorithms and standards are already partly defined. Safecipher and other companies, are already building PKI with NIST approved algorithms. Between 2026-2027, quantum computers may be able to break RSA-2048 encryption, which is described as a worst-case scenario. A conservative estimate places this risk between 2030-2031.
The image features quotes from various experts and reports highlighting the urgency of the situation. For example, a report from September 2016, claims that quantum computing has a one-in-seven chance of breaking RSA-2048 encryption by 2031, with that chance increasing to 50%. Sundar Pichai, CEO of Alphabet and Google, is quoted from Davos 2020, suggesting that quantum computing will break encryption as we know it today within a 5-10 year timeframe. Arvind Krishna stated in May 2018, that anyone wanting to protect their data for longer than 10 years should move to alternative forms of encryption now.
The points and timeline together, paint a picture of an approaching challenge that requires immediate and thoughtful planning to ensure data security in the quantum computing era. Additionally, Stephen Monti of SafeCipher, who has twenty four years’ experience (the author) of building and migrating PKI infrastructure, adds his concern to the incredible challenge of migrating from classical algorithms to Quantum algorithms in enterprise PKI systems.
X