Mosca’s Theorem Overview
Mosca’s Theorem provides a framework to assess the risk and necessary timeframe for transitioning to quantum-resistant cryptographic systems. It posits that an organization’s cryptographic infrastructure is at potential risk if a quantum computer is developed within the period given by the sum of the shelf-life of its secrets and the time it would take to migrate to quantum-resistant algorithms.
The theorem can be distilled into an equation that helps to determine the risk to an organization:
Here is a simplified diagram (below) illustrating the relationship described by Mosca’s Theorem using a timeline
The blue bar represents the ‘Shelf-life of Secrets (x)’ — the time for which the secrets need to be kept safe.
The orange bar represents the ‘Migration Time (y)’ — the time needed to upgrade to quantum-resistant security.
The vertical dashed line represents the ‘Time to Quantum Computing (Q)’ — the estimated time by which quantum computers will be able to break current encryption.
The title of the diagram, “Risk occurs if x + y > Q,” indicates that if the sum of the shelf-life of secrets and the migration time exceeds the time to quantum computing, there is a risk that the data will become vulnerable once quantum computers are available.
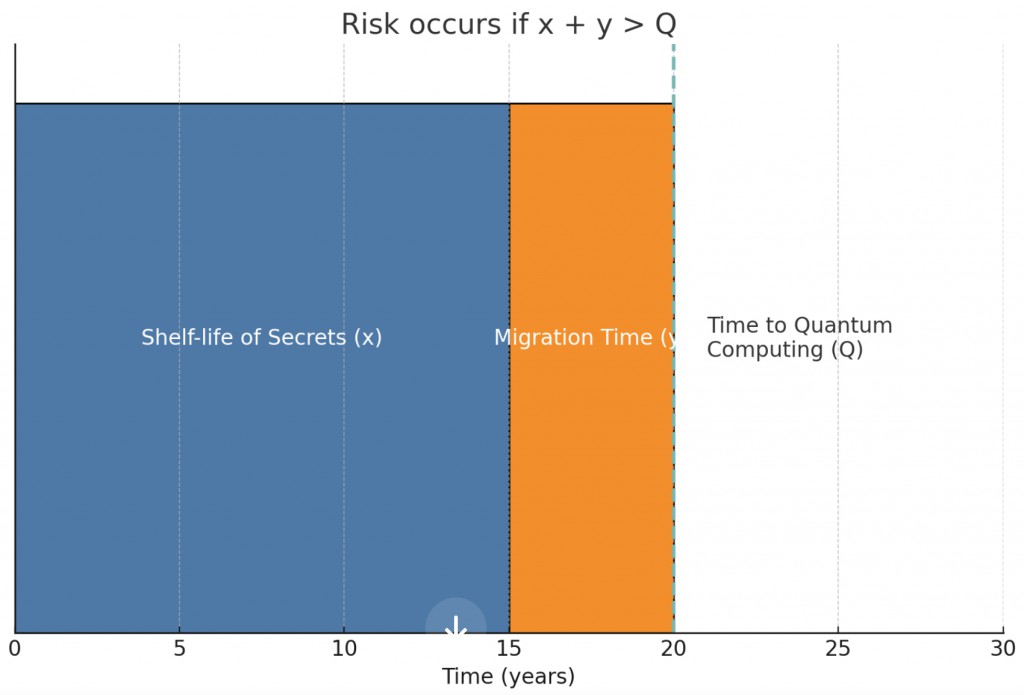
This diagram is designed to convey the concept in simple terms, using ‘x’ and ‘y’ as the lengths of time for each phase and ‘Q’ as the deadline to beat.
When an organization decides to migrate to post-quantum algorithms, it should follows these steps:
Identification
Identify all components that use public-key cryptography. This includes software, hardware, and data protection mechanisms that currently depend on cryptographic algorithms vulnerable to quantum attacks.
Prioritization
Prioritize the importance of each component’s security in the context of the organization’s operations and the sensitivity of the data it protects.
Migration Time
Mosca’s Theorem informs the risk management approach. The organization must assess how long each component’s data needs to remain secure (shelf-life) and estimate the time required to replace or upgrade the cryptographic elements (migration time).
Risk Assessment
They should consider the “risk horizon” — the estimated time until a quantum computer capable of breaking current cryptographic algorithms is expected to be developed.They also need to factor in the “quantum preparation period,” which is the time it will take for the organization to transition to quantum-resistant algorithms.
Based on this risk assessment, a migration strategy is developed. It should include plans for updating cryptographic algorithms, revising protocols, and possibly changing hardware that is not capable of supporting new, quantum-resistant algorithms.
Contact SafeCipher to help you through this entire process
x