What We Do
Primarily, we are crypto specialists with a very specialized knowledge of Public Key Infrastructure (PKI)
Hardware Security Modules (HSM), Quantum Resistant Cryptography, Crypto-Agility, Cryptographic Audits,
Data Protection and Classification from a Quantum Perspective
DATA PROTECTION
We will ensure you are compliant with security standards such as GDPR, FIPS, PCI-DSS and certification to SOC2 and ISO27001 standards covered. We will help you with your compliance and ensure you understand which cryptographic controls you should be using. Contact us for advice and help.
Key Management
Contact us if you are interested in evaluating (or deploying) some of the leading key management systems like: Venafi TPP, SafeNet KeySecure, Thales e-Security keyAuthority, HP Enterprise Secure Key Manager (ESKM), IBM Tivoli Key Lifecycle Manager (TKLM), and EMC’s RSA Data Protection Manager (DPM).
HARDWARE SECURITY MODULES (HSM)
SafeCipher has a continued rapport with all the leading crypto hardware vendors, especially Thales and SafeNet. We have significant experience with these leading vendors and their cryptographic products. We have the experience required to upgrade existing appliances to more current models.
Azure and AWS Crypto Security
Contact us for all your cloud and on-premises HSM, encryption, key management and security best practice requirements. Cloud-based HSM vs. on-premises HSM – how do you choose (ask us for help)? We can help with Azure and AWS encryption, Azure and AWS tenant key management.
Public Key Infrastructure (PKI)
PKI (Public Key Infrastructure) and cryptography is the cornerstone of our business and it is what we have been doing for over twenty years. We can advise you which is the correct path for your business: Public Cloud, On-Premises or Hybrid.
Cloud Cryptography
Key management is the Achilles heel of cloud encryption. Contact us to solve the problem of key management using your own keys. We will guide you through the whole BRING YOUR OWN KEY (BYOK) process.We can help you make the correct choice when approaching the subject of cryptography in the cloud.
Start Preparing for Post-Quantum-PKI Now
xSafeCipher is committed to helping organizations create effective plans that will allow them to transition their PKI and cryptographic estates to quantum – resistant algorithms. This now includes building PKI certificate chains based on Dilithium signature schemes.
x
Quantum Computing and the Need for Organization-Wide Cryptographic Audits
Many organizations have not thought about post-quantum migrations at all, citing the lack of standards — a situation that will change dramatically this year when NIST release the new Quantum Standards. There has never been a more pressing need for organizations to Audit their Infrastructure and Codebase so they can plan and test for migrating to the new NIST approved Cryptographic Algorithms.



We deploy, support and supply all the leading HSMs
and associated crypto hardware.

Public Key Infrastructure (PKI) is the cornerstone of our business. We are fluent in all the leading PKI vendors

Hashicorp Vault (PKI Secrets Engine) and Venafi TPP Integration Specialists
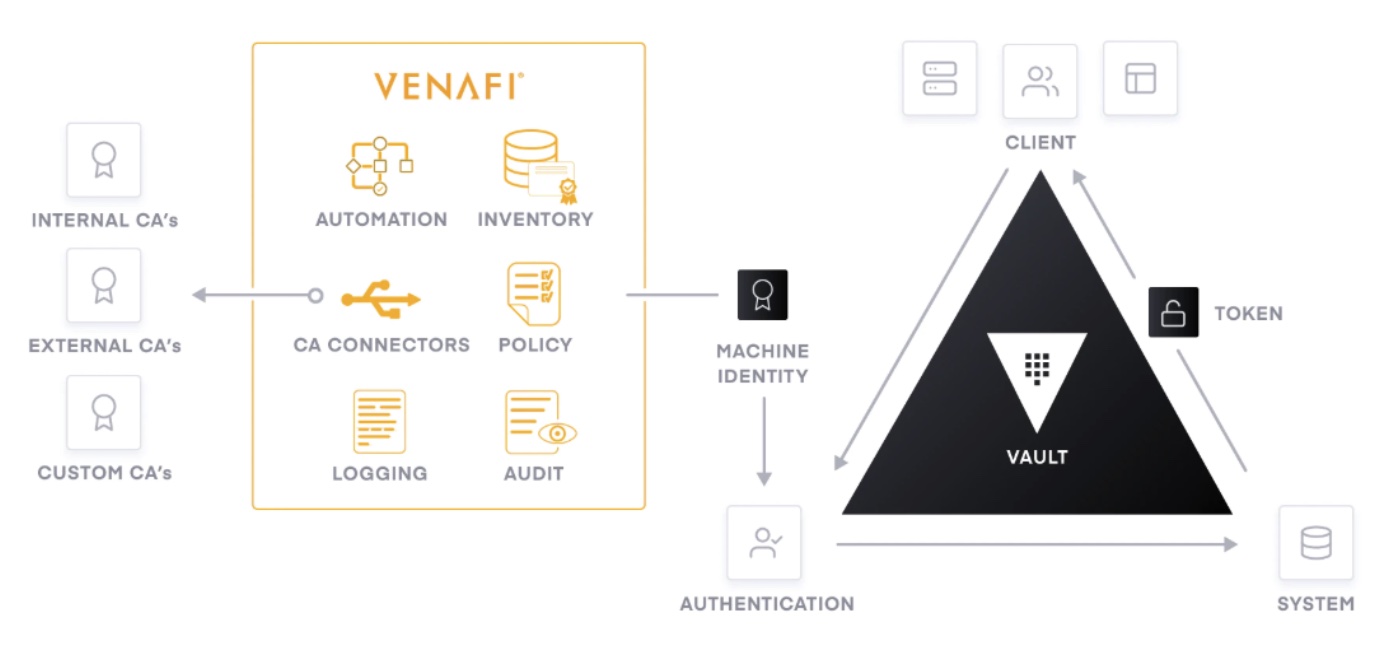
We Work With
All the leading PKI products and all the major HSM vendors.
We use all the leading Key Management products. We deploy in the Public Cloud, On-Premises or Hybrid.




